For the corporate office environment, we are often asked to design and recommend security systems to keep their employees, assets, intellectual property, and physical buildings safe.
These security systems typically include a combination of the following technologies:
- Video Surveillance – comprising IP-based cameras, network video recorders and video management software running on client workstations and/or mobile devices. This may also be cloud-based which would eliminate the need for network video recorders on the premises.
- Access Control – consisting of card readers, electrified door hardware, control panels and access control software running on a server and possibly also a client workstation.
- Intrusion Detection – which includes alarm panels, duress buttons, keypads and sensors for windows, doors, motion and glass breaks.
- Visitor Management System – systems to scan licenses, print visitor badges and manage and control visitor access (visitor management software) plus hardware for dedicated workstations, webcams and ID scanners.

Image from Bernard Hermant in Unsplash
Recently, one of our clients asked us for advice on the most common security monitoring scenarios specifically for offices that do not have a dedicated security team. This is a common question for small-to-midsized companies who do not have the need, budget or resources for a full-time security staff.
“What are the most common security scenarios for offices that do not have a dedicated security team?”
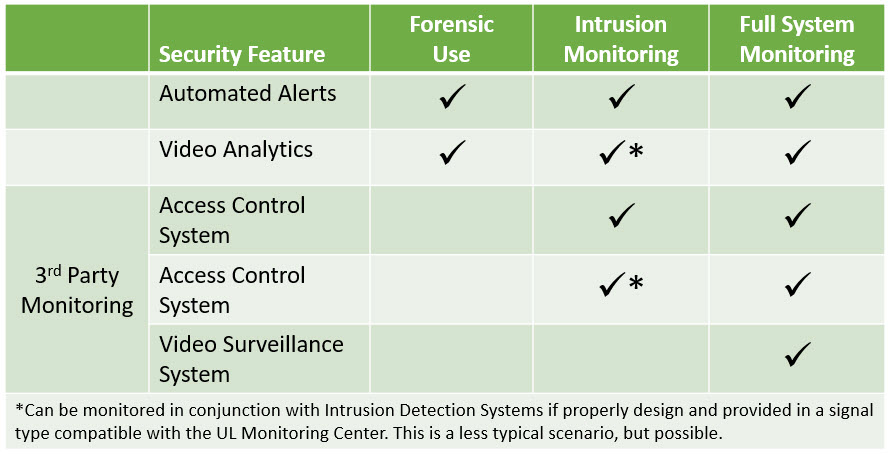
Based on our experience with corporate security systems, the previously mentioned systems are most commonly implemented to perform one of the following three functions when in-house security personnel is not an option:
- Forensic Use (No Active Monitoring)
- Intrusion Monitoring Only (Partial Active Monitoring)
- Off Premises Full System Live Monitoring
Forensic Use
Under the forensic use scenario, the video, access and intrusion systems are programmed to run and record automatically either on-premise or saved to the cloud. The videos are only viewed or retrieved when there is a need to investigate a security event such as unexpected access or a potential theft event. The key here is to automate as much as possible to trigger notifications that can call the attention of a designated user, since the system will not be monitored.
Some implementations include a monitoring screen at the front reception desk for displaying only key camera views, with the understanding that they will not be actively monitored but utilized only as needed. This monitor may be used to view who is at a door before buzzing them in or to identify people accessing areas that they should not be in. While duress buttons at the reception desk can be installed in this scenario, they may just be set up to alert key managers and are not generally linked to the outside world.
Some systems allow office managers or designated users to view live video feeds from a computer, tablet or smartphone to monitor after-hours activity or to check for unusual activity.
Alarms such as motion sensors, glass break sensors or video analytics (for identifying unexpected packages left behind or for virtual fences etc.) can trigger a notification within the security software platform. These alerts are usually programmed to email or text an alert to a designated persons or managers. However not all triggers are required to issue an alert and can be tailored to the company’s preference.
Usually the office manager or site lead is assigned to get the notifications, assess if it requires immediate attention and then phone 911, local law enforcement or the fire department, if necessary.
Intrusion Monitoring
With the Intrusion Monitoring scenario, the security systems are set up in the same way as the Forensic Use scenario. The only difference is that the intrusion detection system is now monitored by a UL-listed alarm and security monitoring company. These are companies who have been certified by UL and follow the most up-to-date applicable codes and standards.
Since the system is monitored by an outside company, the duress buttons can be made operational and can trigger an automatic reaction. The intrusion detection system is connected to the internet to allow a 3rd party to receive the alarms from the glass breaks, motion sensors and duress buttons. This contractor receives those alarms and will follow the designated procedure which could include calling 911 immediately or follow an escalating process where a site-specific person is first called for verification, then 911 if there is no response.
The video and access systems in this scenario are just used for forensic use and are not monitored on a full-time basis. The key here is that the “high priority” system chosen for monitoring is the intrusion system only, which would alert the UL monitoring center of any unauthorized access.
Full System Live Monitoring
Under the Full System Live Monitoring, a UL-listed company actively monitors the entire system including video feeds. They not only respond to system triggers and alarms but also are viewing your cameras in real-time to spot any unauthorized access or behavior.
Their responsibility is to monitor alarms and video feeds in order to alert the site manager and authorities of issues or contact 911 as they happen. These companies do not take over administrator rights for the system and do not manage providing access levels and badges. They are only there to monitor the alarms and video feeds.
The visitor management system is typically implemented independent of the scenarios above since an alarm monitoring company would not typically monitor or manage this system. Most small to midsized companies that opt to implement this system do so to facilitate or speed up their visitor sign-in process.
How Do You Decide Which Security Monitoring Scenario is Right for Your Company?
The final decision on which corporate security system scenario is best for your company should be based on analysis of several factors including:
- Budget or resources available
- Risk profile of your location or building
- Value of the assets in your office, including physical, inventory, files or intellectual property
- Risk appetite or the amount of risk your organization is prepared to accept
- Policies and procedures the organization has in place or will put in place
After a careful analysis of these factors, the answer to this question usually becomes obvious. In addition, all security systems designed and deployed should always be supported by a policy and procedures.
“All security systems designed and deployed should always be supported by appropriate security policies and procedures.”
Mike Niola, Associate and Vantage Technology security expert