A large part of our journey in information security has been about moving from a disjointed set of activities to creating a program. Nearly all institutions have information security policies and procedures. Leadership recognizes the necessity of security. Projects are taking place, but the efforts lack cohesion. This familiar scenario describes security organizations that are in the early stages of maturing into a formal program.
What is a program?
The first step in making progress is to understand what a program is and why it is needed. The term ‘program’ is often used, but not well defined. A program is an organizational effort designed to meet an overarching goal. There are a few ways to recognize when organizational efforts rise to the level of requiring organization into a program. These attributes are often associated with program level activities:
- Efforts that are important to the mission of the institution
- Efforts that are seen as ongoing
- Efforts that are complex and widespread
- Efforts that require significant organization
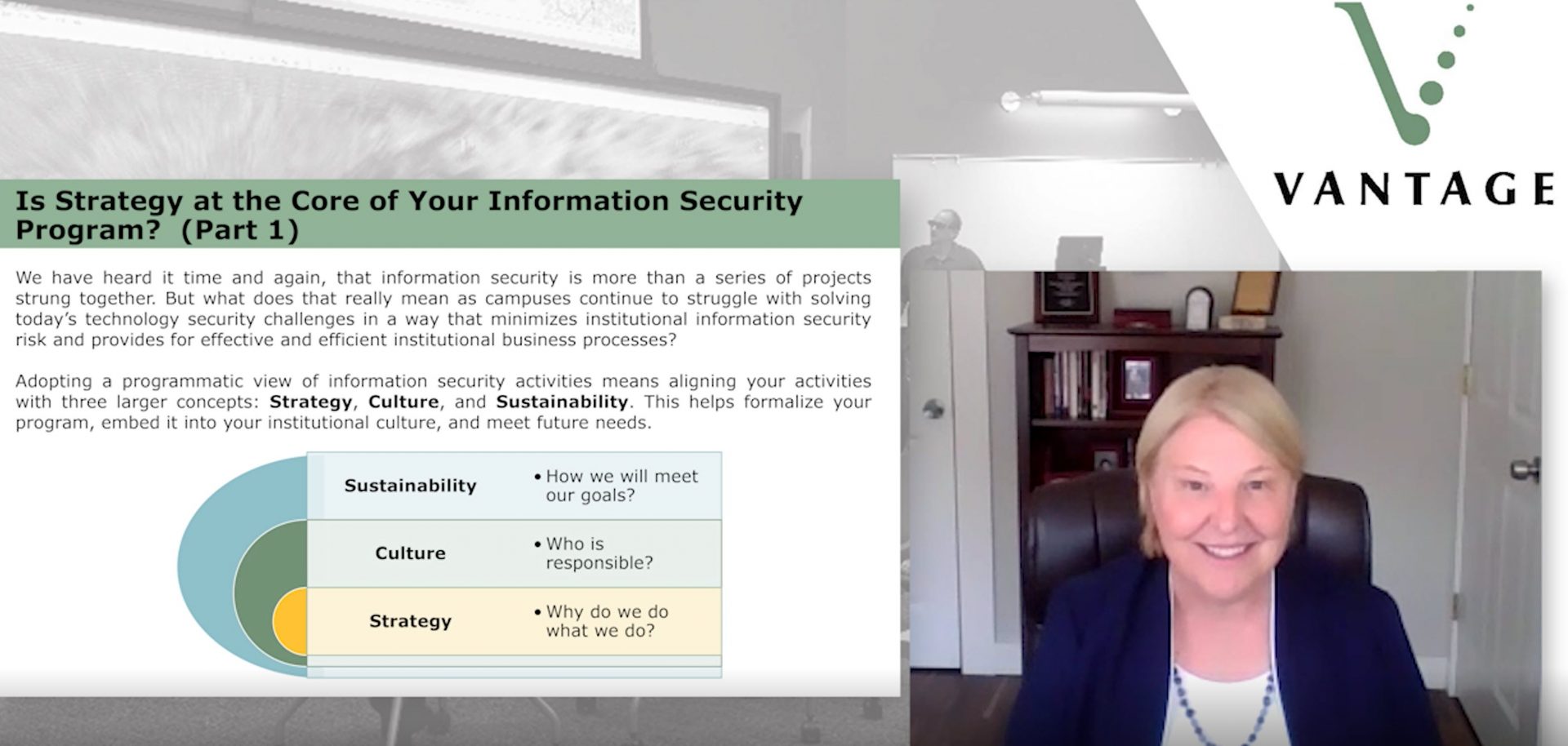
Certainly, we agree that information security is important to the mission and requires ongoing efforts. Historically, that has been achieved with policies, short-term projects, and small immediate goals. However, institutions now face ever-increasing complexity in information security needs and require widespread efforts across the institution to successfully achieve goals and manage information security obligations. This is why information security must evolve into long-term programs with a mission, goals and strategy that improve the security posture of the organization. A mature program offers services that form a cohesive and coordinated effort to support the mission of the institution in a way that is understood and leveraged by users.
How is a program created?
As institutions decide to define an information security program, they should use a program charter to address these questions:
1. Why are we undertaking this program?
A program’s ‘why’ is all about purpose and strategy. Programs are based on fulfilling an ongoing need, which is often clearly described in the program purpose. Mission statements are often used to represent program purpose. A mission statement might, for example, state support for the institution’s research and education mission by enabling the campus community to mitigate risk to information assets. A crucial element of the charter includes allocating responsibility and authority for implementing and overseeing the program. Authority creates accountability and can be defined in policy or delegated to a role by institutional leadership.
Principles and objectives help to form the unique strategy that fits program needs to the specific institutional environment. Strategy must be at the core of your information security program and guide all layers that are created thereafter. It explains why the program exists–not for its own sake, but for the institution.
2. Who is responsible?
The ‘who’ portion of a program is all about creating an organizational culture of shared ownership of security risks. Program success is dependent upon campus member participation. Campus members must understand the values and behaviors that are required as part of their roles and responsibilities. Defining the roles and responsibilities, as well as clear program structures, like committees and governing processes for working together, helps individuals navigate the complex and widespread responsibilities associated with information security. Program structure and associated roles and responsibilities provide the necessary organization to coordinate program efforts. Embedding information security into your institutional culture helps ensure institutional buy-in and importance. Everyone has a role in information security.
3. How will we meet our goals?
Finally, the ‘how’ portion of the program creates program sustainability by creating program plans, processes, metrics, and assessment. At this level, the program strategy and structures are relied upon to move from disjointed activities to cohesive plans. Efforts should be communicated, transparent, and clearly fall under one or more overarching objectives. This provides an opportunity to examine where current efforts serve the program objectives and where they may not be contributing good value in their present form. Having a solid foundation of strategy and culture creates an opportunity to reevaluate options for achieving the program objectives, prioritizing efforts, and communicating them in ways to help users understand how the individual project efforts are related to achieving program objectives. Planning for program sustainability means the ability to show that the institution is meeting its information security goals. It helps you answer, “are we more secure today than we were yesterday?”
In order to be truly sustainable, programs require a continuous improvement cycle where plans are made, communicated, implemented, and assessed on how well efforts are helping achieve those overarching objectives. The program itself also requires periodic review and renewal based on current environment situations and institutional need.
A well-defined charter can provide the value proposition that you intend to bring to the campus with your information security program. Taking the time to create a program charter will help you formalize your program, turn the corner from reactive to proactive, embed information security into your institutional culture, and meet future needs.
This post was authored by Vice President Cathy Bates, who advises clients on technology strategic planning, information security, and initiatives that transform institutional academic, administrative, and research capabilities. A former CIO, Cathy speaks and writes frequently about how to build and sustain effective organizations and programs. Connect with Cathy via LinkedIn.