October is National Cybersecurity Awareness Month (NCSAM). Vantage recognizes the importance of everyone being safe and secure online. Because of our involvement and interest in cybersecurity and information security, we became 2018 NCSAM Champion. As our commitment as a NCSAM Champion, we have pledged to publishing a weekly blog post on a different cybersecurity topic.
This week’s post was authored by Senior Consultant Joanna Lyn Grama and is based on her recent campus presentation for The Ohio State University Cybersecurity Days on consumer data privacy titled Is the refrigerator listening to my conversations again?.
Connected Devices, Connected Data
Sometimes I shudder at the digital footprint that I leave through the services and technology that I interact with daily. For example:
- My cell phone is the command center for my data driven life, serving both as an assistant (Hey Siri!), health coach, and media communications hub
- Netflix really gets me and always recommends shows that I end up liking
- My addiction to social media and online shopping means that there is never a shortage of online advertisements featuring products that I desperately need right now
The number and types of devices that connect to the Internet and provide us with functionality and access to services, and convenience, are growing. In addition to the connected audio devices like Amazon Echo or Google Home, there are smart locks that can track my comings and goings, light switches and plugs that can be controlled remotely, a smart brace for my knee that alerts my doctor when I haven’t done my physical therapy, watches that track physical activity including heart rate and sleep patterns – and refrigerators that are smart enough to tell me where my family members are and if I need to pick up OJ on my way home from work. You can even buy a connected teakettle! All of these devices and services collect personal data that is either sensitive or confidential on its own, or sensitive and confidential when combined.
By 2020, it’s estimated that for every person on earth, 1.7 MB of data will be created every second. I contribute to these statistics (and the data that these services generate) daily:
- 8 billion humans use the Internet
- 64,619 Google searches every second
- 2,083,333 Snapchat snaps shared per minute
- 473,000 Twitter tweets per minute
It is heady to think about all the transactional data collected by devices and service providers, as well as the picture that service providers already have about me based on my interactions with them.
With All This Data, Someone Will Figure Out a Way to Steal It
Allegedly the famous U.S. bank robber Willie Sutton said he robbed banks because “that’s where the money is.” Today data is money. Most of us worry about breaches of our personal and confidential information like Social Security numbers, credit card numbers, or financial account information. Since the massive Target breach in 2013, it feels like not a day goes by without hearing about a data breach at a company or governmental entity. It can be distressing to receive yet another data breach notification letter in the mail.
Unfortunately, there are plenty of data breaches to study. The Information is Beautiful website provides a delightfully detailed and filterable view of the World’s Biggest Data Breaches from 2004 through 2017. When you have a few moments to spare, it is fascinating to view the number and magnitude of data breaches by industry and type of breach.
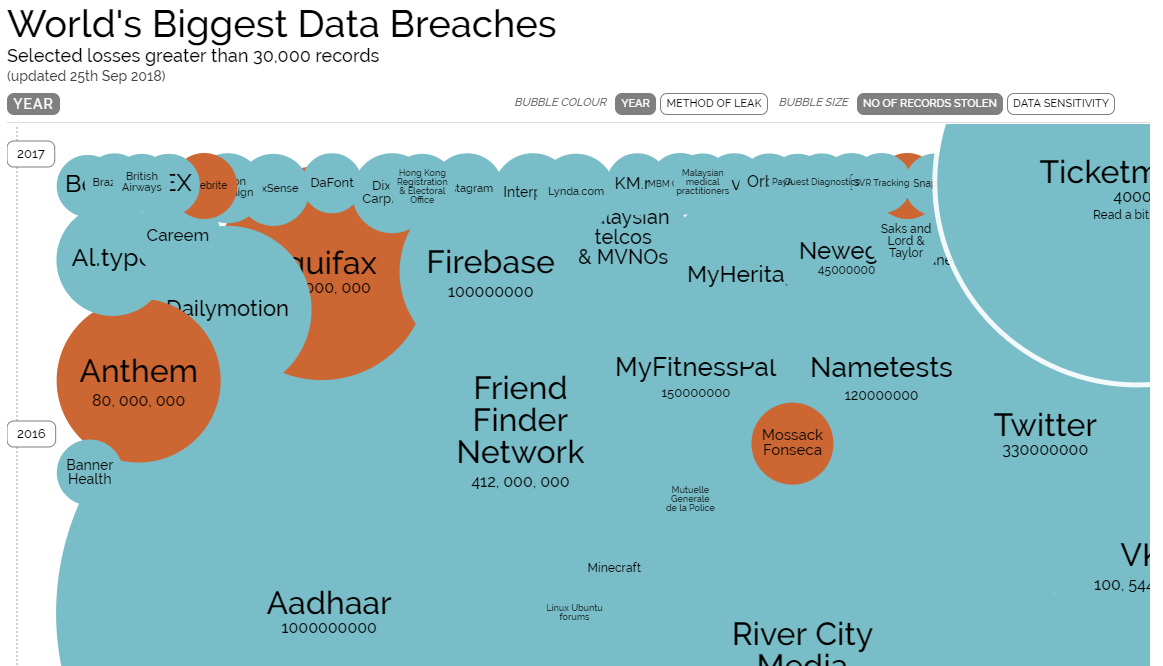
World’s Biggest Data Breaches – from Information is Beautiful (
Another source of data breach data is the Privacy Rights Clearinghouse (PRC). In 2017, they noted that a little over 800 breaches were made public representing over 2 billion records. While about 50% of the raw number of breaches involved hacking, over 80% of the total records exposed in all breach incidents were attributed to unintended disclosures. Unintended disclosures tend to be preventable. They are those disclosures where information is improperly posted on a website, transmitted to the wrong party by e-mail, fax, or mail, or otherwise mishandled.
What’s a Consumer to Do?
I have covered a lot of ground this post. My intent was to provide an overview of how much personal data is being captured on each of us and how rapidly this type of data collection might grow over the next decade, and some data breach statistics. There are some laws that help protect different types of consumer information. However, there is no one comprehensive U.S. law protecting an individual’s personal data. Instead most U.S. laws are directed toward specific industries and specific types of data. This has led to a fairly complex “patchwork quilt” of data security and privacy laws.
There are some steps that consumers can take, however, to protect their personal information. My top personal tips are:
- Read the “Terms and Conditions” for services, devices, and apps every single time. Even if you ultimately choose to allow a service, device, or app to use your personal data, it is important to understand what exactly you are agreeing to
- Trust sparingly and verify. It’s OK to ask merchants and service providers how they intend to use your data and who they plan to share your data with. It’s also OK to decide that you don’t want to share your data (and be prepared to walk away from the device, service, or app if necessary)
- Use different levels of passwords for different accounts (and use a password manager to manage them all!) If a service or device offers multi-factor authentication, then implement it



