A favorite information security professional saying is “information security is a process, not a project.” The notion of information security as a process conjures a continuing progression of activity (which might even be a project or two) designed to meet a specific objective. But thinking of information security as a process is not enough to ensure that a college or university is effectively addressing the many threats that it faces each day. Instead, information security processes must evolve into long-term programs with a mission, objective, and strategy that is aligned with institutional goals. Programs are enduring because they address complex and ongoing issues and include a notion of continuous improvement and progress. What does an information security program look like at a higher education institution?
Campus Information Security Program Components
Higher education information security programs do a lot of heavy lifting, from educating students, faculty, and staff about security hygiene, to running research computing networks, to investigating information security incidents. The spectrum of services that must be offered is wide and generally fall into 5 basic categories:
-
Strategy
-
Management
-
Policy and compliance
-
Awareness and training
-
Services and operations
Strategy
The strategy component of an information security programs looks at how the institution sets its information security program goals and defines what success looks like. The institution’s information security strategy should support the mission, strategic objectives, risk posture, and compliance obligations of the institution. The institution’s strategy can also include distinct leadership elements like adopting a campus culture of shared responsibility for information security, or the naming of an individual with institution-wide responsibility and authority for information security written into their job description. (EDUCAUSE has data on that, reporting that 41% percent of institutions have a dedicated person whose primary responsibility is information security.)
Management
The management component of an information security program looks at the critical security service areas provisioned by the institution. Is the institution performing the types of activities and offering the types of services that we would expect an institutional information security program to offer? And, is the institution resourced effectively to provide those services—either in-house, with shared service models, or with outsourced assistance. Institutional information security service areas may vary depending upon institutional needs, but almost all institutions must account for risk analysis, asset protection, incident response, education and awareness, and business continuity functions within their overall information security program.
Policy and Compliance
Policy and compliance components review how an institution formalizes its information security policies and ensures compliance with legal and regulatory obligations. Policies set forth permitted (and forbidden) activities, reflect how an organization protects its own data and the data of others, document compliance with legal and regulatory requirements, outline employee responsibilities, and state the consequences for failing to meet information security responsibilities. That’s a lot of one, or a couple, of documents to address. As the operational and threat landscape in higher education has gotten more complex, policies and the policy making process must respond in kind—evolving from topic-specific tomes to living, framework-based documents that provide the flexibility needed to respond to institutional risk in a coordinated and holistic way.
Awareness and Training
The awareness and training component looks at how the institution provides information security education to campus community members. We know from EDUCAUSE that 85% of institutions have mandatory information security training for faculty and staff, and 49% of institutions have mandatory information security training for students. These statistics are great because good information security hygiene habits can help improve the information security health of the entire campus community—whether at work, home, or while in class. Many colleges and universities are starting to move beyond basic information security awareness activities and are providing detailed security technical training to end users with privileged access. Some institutions are even encouraging third parties that are authorized to interact with institutional systems to receive applicable training.
Services and Operations
Services and operations components look at how the institution uses specific services and technologies to secure institutional resources and data. There is a plethora of services that institutions deploy, from logging systems, DLP, ticketing systems, firewalls, antivirus and antimalware, and so on. Many of these services are completely invisible to end users, working silently in the background to ensure that the institution and its data are as secure as possible. I often think about services and operations according to the NIST CSF framework (EDUCAUSE tells us that about a third of institutions use this framework for their information security programs) because analyzing services provides structure. Using such a structure may help an institution identify places where it has operational gaps.
Using Governance Process to Improve Campus Information Security Programs
Setting up an information security program doesn’t happen overnight and ensuring an effective information security program shouldn’t be left to luck. Instead, common governance processes can be used to help an institution evolve its information security program.
“Governance” means all the things that institutions do to coordinate and control its actions and resources. Put simply, governance is a process for decision-making and the implementation of decisions. In higher education, we expect governance processes to be transparent, responsive to stakeholder needs, inclusive, and effective. When speaking of information security, governance processes help institutions take a step back from the project aspect of information security and instead allow examination of both the technical facets of progress and the influence of institutional culture.
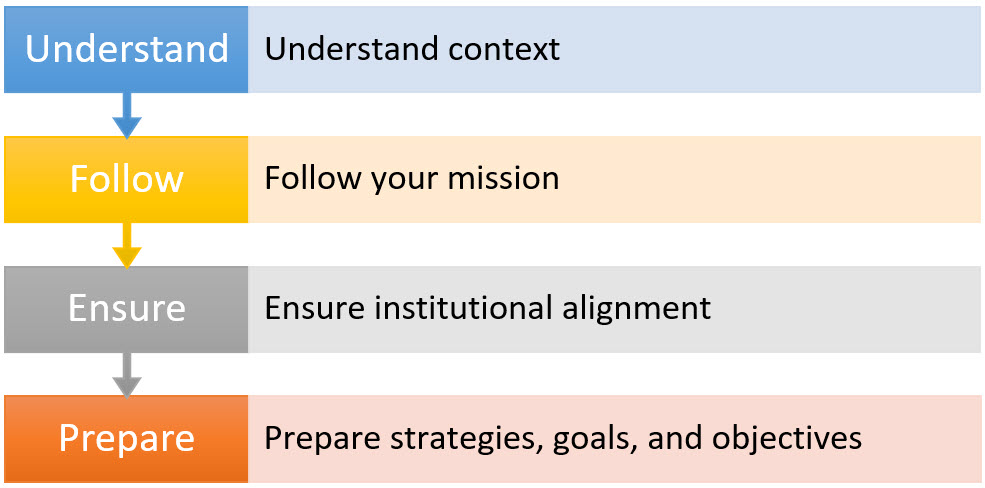
To move information security programs forward with governance processes, institutions can:
-
Understand context
Do you understand the magnitude of your institution’s dependency on IT to conduct academic, research, outreach programs, and to offer support services? How sensitive are your stakeholders to security and privacy issues? Is your institution part of the national critical infrastructure? Do you have a unique mission, like a multinational presence, that relies on technology to meet the mission? Use your understanding of institutional context to help outline what is important for your information security program.
-
Follow your mission
Security doesn’t exist on its own accord—it exists to enable the mission of the institution. Missions provide direction and purpose to keep you on track when the going is tough. Be sure the information security program mission is consistent with the mission of the institution. It also doesn’t hurt to keep mission statements short and sweet, and to revisit them from time-to-time.
-
Ensure institutional alignment
This item is slightly different from mission alignment. This step asks how well you achieve your objectives while achieving balance among varying and potentially competing stakeholder information security needs. Are you addressing information security risks and challenges in a way that meets your objectives?
-
Prepare strategies, goals, and objectives
Strategies define how you satisfy your mission, goals state what must be done to implement the strategy, and objectives are the actions and tasks that need to take place to meet a goal. In short, do you have a plan for how you are going to achieve your desired end-state? A little planning can go a long way in improving information security program maturity and reducing institutional risk.
Higher education campus IT environments are rapidly changing—from the implementation of sophisticated enterprise systems to the purchase of third-party products and services that use institutional data. This rapid pace of change and the growing complexity of security threats facing campus IT operations requires a concerted focus on information security program success. Institution’s can confront these challenges and move their information security programs forward by using traditional governance concepts.
Senior Consultant, Joanna Grama, recently spoke at the Kentucky Cybersecurity Summit, hosted by the Kentucky Community and Technical College System. The above blog is excerpted from her presentation, “Get Your Governance On: Using Governance Processes to Mature a Campus Information Security Program.” Joanna advises clients on technology strategic planning, information security, and privacy initiatives.