Many networks evolve organically. In higher education, universities built their networks in the 1970s and 1980s and have upgraded them in place, often using the same approaches for the last several decades. Although technologies have changed considerably, funding models have lagged, and the lack of a sustainable funding model has resulted in unsustainable levels of deferred maintenance and technical debt that impair institutional success, with IT leaders receiving just enough funding to keep the network running. These campus environments are a mix of new equipment (often acquired out of necessity) and old equipment, some of which is no longer supported by the manufacturer and present significant security risks.
As organizations reach a tipping point, the only viable option forward is to modernize the network.
A network modernization project is a combination of improving the efficiency of network operations, improving security, reducing institutional risk, and a basic plumbing project to keep the transport that a network provides functioning at a high level. The goal is to create a network environment with the capabilities to enable institutional research, academic, and administrative missions over the long term. Combined with forward-looking financial planning for a sustainable funding model, the historical cycle of technical debt and deferred maintenance can be broken.
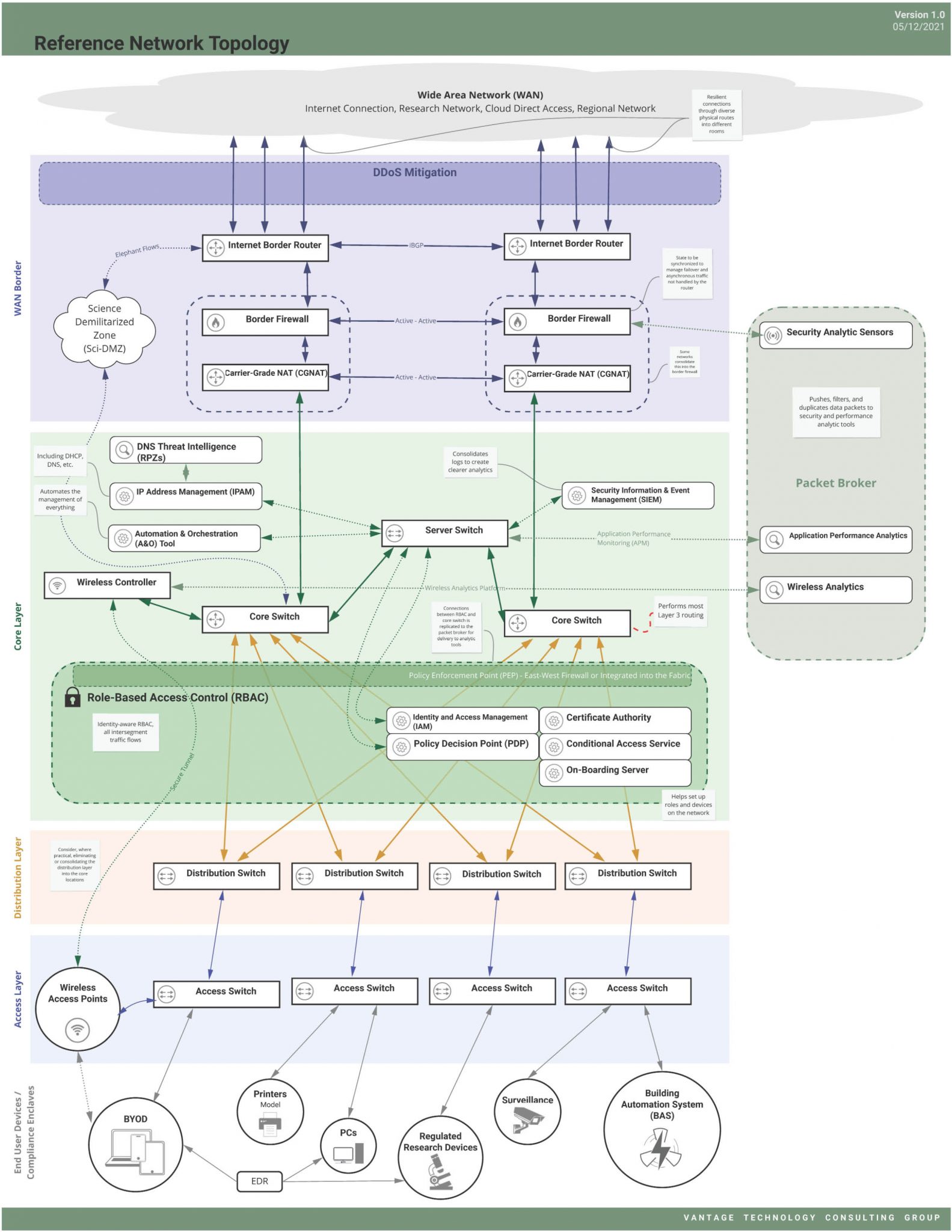
We’ve found that there are commonalities – key design elements – to most future higher ed architectures that should be considered during a network modernization project, which we describe in our reference architecture (Figure 1).
Key Design Elements You Should Consider for Your Network Environment
Most networks have a common set of basic design elements, such as Internet routers and firewalls, fabric (core through access switches), Wi-Fi access points (APs) and controllers, and monitoring/management systems. Beyond those basics are a host of technologies that are transforming campus networks by increasing resiliency and efficiency, strengthening security, and making management much easier.
Automation & orchestration (A&O)
Common network management practices still suffer from a reliance on manual operations. Transforming manual operations and business rules into automated IT services introduces standardization and reduces the risk of human error. Whether using a vendor-centric or open approach, we think A&O is crucial to the success of any modernization effort. The A&O tool should work with the rest of the network and application stack and tie into orchestration engines used across IT. A&O also lets you move closer to “network as code,” where network configurations and services like routing, load balancing, and security are managed more like software development. As an institution’s A&O expertise matures, opportunities abound to incorporate DevOps approaches that orchestrate between the network and related systems, storage, virtualization, public and private clouds, and more.
Identity-aware networking, role-based access control (RBAC), and Zero Trust (ZT)
Our vision begins with microsegmenting the network and granting access to network resources (segments) based on knowledge of the user and device combination (the role). A policy enforcement point (PEP) as defined in NIST SP 800-207 (Zero Trust Architecture) such as a firewall or even the device posture and conditional access logic. (See Figure 2) Add to the ecosystem something like user/device certificates (802.1x EAP-TLS) and you have built an effective way to authenticate and authorize access to network resources. You’ve also built something that can be leveraged for ZT networking and password-less access to applications (no more VPN!), improving the user experience and security at the same time.
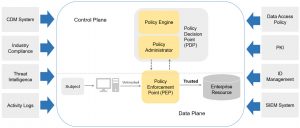
Figure 2: Core Zero Trust logical components; Source: NIST SP 800-207, Zero Trust Architecture, Figure 2.
Broadly, there are several distinct ways to implement RBAC based on manufacturer support, which include:
- Non-proprietary: All inter-segment (inter-role) traffic flows through east-west firewall(s) as the PEP. A policy engine like ClearPass or Cisco ISE in conjunction with 802.1X provides the fabric with the information to dynamically place objects in the correct role/segment and the next-generation firewall (NGFW) to apply appropriate role-based rules. We see this approach most commonly when the decision is made to be multi-vendor or getting RBAC-capable access switches fully deployed will take longer than the institution can wait to begin achieving RBAC value.
- Cisco Software-Defined Access (SDA) with scalable group tags (SGTs): When a device connects to the network, Cisco ISE acts as the policy decision point (PDP) and applies an SGT as a role. The tag remains on packets (associated with the role) as they travel through the network. The network fabric acts as the PEP, based on SGTs acting as a role definition. This is most applicable in a full-stack Cisco environment and requires current-generation access switches as well as specific Cisco licenses.
- Aruba: Traffic is tunneled back to the controller (both wired and Wi-Fi) where the controller acts as the PEP, applying a variety of firewall-esque features. The need to tunnel all PEP traffic back to the controller cluster can be challenging for particularly large institutions. This approach also implies the access switches are all Aruba (not legacy HPE). ClearPass would typically act as the PDP.
- Extreme and Alcatel-Lucent (ALE): Both have approaches where the PEP is at the network ingest (typically the access switch and Wi-Fi controller). Like the other approaches, all access switches need to be capable of acting as a PEP.
Outside of higher ed, the trend is to move towards a client-centric model where endpoint software is used on every device to manage access. That can work effectively when most endpoints are centrally managed and standardized but does not tend to fit the realities of higher ed. Implementing RBAC is a huge enabling step in the evolution toward Zero Trust networking by rethinking the way network-accessible applications authenticate and building key infrastructure that can be leveraged for ZT. Effective ZT also implies an effective identity access management (IAM) environment that can be relied upon to provide accurate authorization information. It is our experience that, aside from funding, IAM is the most challenging issue on the road to ZT in higher ed.
Analytics, sensors, and packet brokers
Effective analytics tools are far more than just monitoring tools. They can correlate information in innovative ways to provide prioritized and actionable information we only dreamed of a decade ago. The tools today are by no means a panacea and the true “single pane of glass” often remains elusive, but the impact of adding effective analytics can provide insights that revolutionize our practices. For example, analytics tools enable us to proactively know that a specific anycast DNS server is responding slowly to certain clients or to measure the impact to the client experience of tweaks to Wi-Fi parameters.
Continuous network monitoring and analytics tools that provide deep visibility are needed to avoid outages, maintain high performance levels, and provide the ability to recover more quickly should an outage or incident occur. Similarly, application performance analytics point to the cause of performance problems in the network. We consider these types of analytics tools to be quick wins with outsized benefits for institutions. The tools are relatively easy to install and use, typically generate critical network insights soon after installation, and are highly useful for troubleshooting. Effective analytics also create efficiencies that can save considerable money in right-sizing the timing and scale of upgrades and validating which potential approaches work. Tools like Nyansa Voyance (now owned by VMware VeloCloud) are often powerful additions to the analytics toolbox.
Security analytics are an essential part of layered network security to detect potential threats. They also help institutions meet compliance obligations, such as NIST 800-171 (Controlled Unclassified Information (CUI) and Sensitive But Unclassified [SBU]), which is typically a component of the contractual obligations for federal funding such as those gained through financial aid and research grants.
To achieve the best visibility, data is collected from multiple sensors at critical junctures throughout the network. Some institutions use a packet broker to consolidate, duplicate, filter, and push data packets to the right security and performance analytic tools, maximizing visibility while minimizing analytics sensors. Packet broker examples include DANZ (formerly Big Switch Monitoring Fabric) and Gigamon, while examples of network analytics tools include Zeek and Suricata. Some of these tools can also provide key insights when dealing with a potential security incident to help determine if any data was exfiltrated.
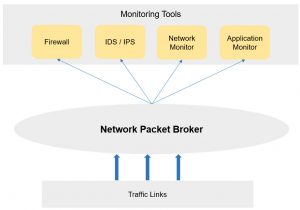
Figure 3: A packet broker conditions traffic and pushes it to the right analytics tool.
RPZs in DNS
DNS Response Policy Zones (RPZs) represent a comprehensive tool for blocking DNS resolution to known malicious hosts and sites. By configuring a local RPZ or subscribing to a service, RPZs in DNS prevent some malicious traffic from gaining a foothold. For example, including an open source threat feed of known command & control (C&C) servers can block DNS resolution of those domains and provide actionable intelligence about which clients may be infected. Implementing RPZs is typically very low cost and a high value option.
Distributed denial of service (DDoS) mitigation
A DDoS mitigation service limits the impact of DDoS attacks, keeping the institution online. A service can protect a subset of IP addresses or an entire campus network. Deploying a DDoS mitigation service typically requires the installation of an appliance at the Internet border, which monitors and cleans a certain volume of traffic. When the appliance detects more DDoS traffic than it can handle, Border Gateway Protocol (BGP) advertisements are adjusted to reroute traffic through a more elastic cloud scrubbing service. In some cases, the regional education network that the institution gets Internet access from may offer effective DDoS mitigation services. These services are not inexpensive and are often value-engineered out until an impactful DDoS event occurs.
We’re Here to Help
Understanding your major pain points, how to overcome them, and determining how your future network should function is challenging for any IT department to work through on their own. Vantage has completed several network modernization projects – we know what your peers have deployed, what works and what doesn’t, and how to help you customize a plan that is right for your environment.
Learn more about how we helped a higher education institution revolutionize their campus network
This post was authored by Associate Vice President Jon Young, and Consultant Kim Lindros.
Jon advises clients on network modernization, technology strategic planning, and initiatives that transform institutional academic, administrative, and research capabilities. Jon is a member of the EDUCAUSE communications infrastructure and applications (commtech) CG steering committee.
Kim supports clients and our consultant team with technical writing, documentation assistance, research, and report preparation. She’s written numerous pieces on security, technology, and the impact on higher education.